P3 1-2/2021 en
Emotet & Co.
Risks and Impacts of Malware in Industry
Management & Marketing
Viruses and worms are no longer just targeting financial and business systems. In recent years, it has been increasingly observed that malware was used to compromise production processes and earn money with it. This is achieved by manipulating or delaying data flows.
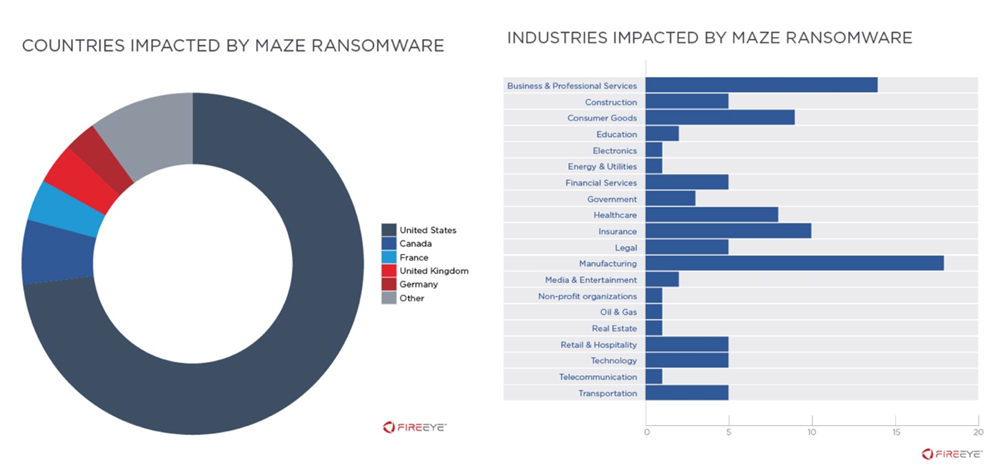
Maze: Impact by country and industry.
The processes and supply chains in industrial manufacturing are based on huge amounts of data. Systems for managing business processes such as customer orders or stocks provide the data for automation systems that are used to maintain production. The number of such systems is steadily increasing, since producing more products for more customers requires increased efficiency, which is achieved through extensive automation in data transmission and processing as well as in production itself. In view of the rapid processes that are largely beyond human intervention, even minor manipulations of the data can lead to considerable financial damage. In extreme cases, hackers can use these manipulations as part of a more complex attack in order to endanger the existence of the company or even human life.
Maximum damage in production technology
According to a study by Forrester1, 96 percent of all German companies have been the target of a business-damaging attack from the Internet. For many years, ransomware attacks have mainly targeted individuals and businesses with financial or personal information. But in the meantime hackers have recognized that they can use the same methods to stop or delay production processes and thus also achieve a financial gain in production technology2. To do this, they attack systems that interact directly or indirectly with operating technology: engineering workstations, human-machine interfaces, data storage and systems for supervisory control and data acquisition (SCADA). Around 18 percent of the organizations affected by the “Maze”3 ransomware last year can be attributed to manufacturing companies; they are thus the most severely affected industry. Not surprisingly, if you have extortionate intentions, you won't care what kind of processes you interrupt as long as you benefit from them.
IT / OT integration as a gateway for hackers
There are many reasons for the high number of cases in which criminal hackers target manufacturing companies. Among other things, they are related to changes in the technologies and infrastructure used by companies. Information technology (IT) and operational technology (OT), which are used to control and monitor production systems, have been converging for a number of years. Due to the increased IT / OT integration, new gateways for potential security threats have emerged. The impact depends on the methods the hackers use to break into their victim's network and at what stage in the production and supply chain the malware is accessing. Depending on the situation, either throughput and production quality are already suffering, or the goods do not reach the customer on time or to the agreed extent.
The disruption can either be traced back to an obstruction of the IT, i.e. the flow of data to the production processes is disturbed or interrupted, or the error occurs in the OT, where the production systems are simply not prepared for unexpected interventions by malware or other external influences. Errors in processes supported by OT can have a particularly negative impact on production and, under very specific circumstances, even lead to damage to the infrastructure or injuries to employees.
Ransomware threatens manufacturing
One of the greatest threats currently facing manufacturing companies is ransomware, a form of malware. Financially motivated hackers often seek access to corporate networks in the manufacturing industry using methods such as social engineering or phishing attacks. Once the attackers have access, they move through the network, overriding the security mechanisms and encrypting all files they find. At the end of the day, the victim receives a ransom demand, which has to be fulfilled in order to get the encrypted data released. It also happens that the hackers post confidential or personal data on public websites in order to blackmail their victims. Examples that have made headlines lately include WannaCry, LockerGoga, Ryuk, Maze, and Egregor, among others.
The hackers use various tools to gain access to the networks of their victims and to prepare the attack. A very well-known tool is the Emotet malware, which was recently destroyed in an international campaign. “The clients for such campaigns are various criminal groups that have used Emotet as malware-as-a-service,” reports Kimberley Goody, Senior Manager of Cybercrime Analysis and Threat Intelligence Expert at FireEye.
Whether the smashing of Emotet will have a long-term calming effect on the ransomware scene depends above all on whether the actual masterminds have been arrested. “In the past, hacking groups kept rebuilding their botnets,” Goody noted. There are now partnerships between Emotet and other malware campaigns such as Trickbot, Qakbot and Silentnight, from which new spamming attacks could be launched.
The SOC is often overwhelmed
The Security Operations Centers (SOC) already established in many companies can hardly cope with the growing flood of malware. The main culprit is the increasing complexity, because the hackers use different types of tools - from disguised malware to open source or commercially available software. In addition, the Covid pandemic has banned many security experts to working from home. According to a study by the Ponemon Institute4, commissioned by FireEye, this has a negative impact on the performance of the SOC in every second company.
The SOC teams are all highly paid specialists who are heavily wooed on the job market because demand is constantly increasing. This leads to a high fluctuation in the teams. At the same time, the tasks are becoming more and more demanding, which is why the effect that the work of the SOC has on company security diminishes. 51 percent of the participants in the Ponemon study stated that the return on investment (ROI) in the SOC was getting worse instead of better.
Solutions to the dilemma
The security experts in the companies are often busy with manual routine work, which further reduces their efficiency. New technology such as XDR systems (Extended Detection and Response) can largely relieve them of this. A whitepaper by Mandiant Threat Intelligence5 offers useful tips specifically for dealing with ransomware.
According to the Ponemon Institute, the cost of a cyber attack to those affected already averages 3.86 million dollars - and the trend is rising. So it makes sense to consult the know-how of external specialists in order to check your own security mechanisms or - if the worst comes to the worst - to limit the damage. In any case, manufacturing companies shouldn't take the growing malware threat lightly.
1 https://de.tenable.com/analyst-research/forrester-cyber-risk-report-2020
2 https://www.fireeye.com/blog/threat-research/2020/02/ransomware-against-machine-learning-to-disrupt-industrial-production.html
3 https://www.fireeye.com/blog/threat-research/2020/05/tactics-techniques-procedures-associated-with-maze-ransomware-incidents.html
4 https://respond-software.com/resources/reports-ebooks/second-economics-of-the-soc/
5 https://www.fireeye.com/content/dam/fireeye-www/current-threats/pdfs/wp-ransomware-protection-and-containment-strategies.pdf